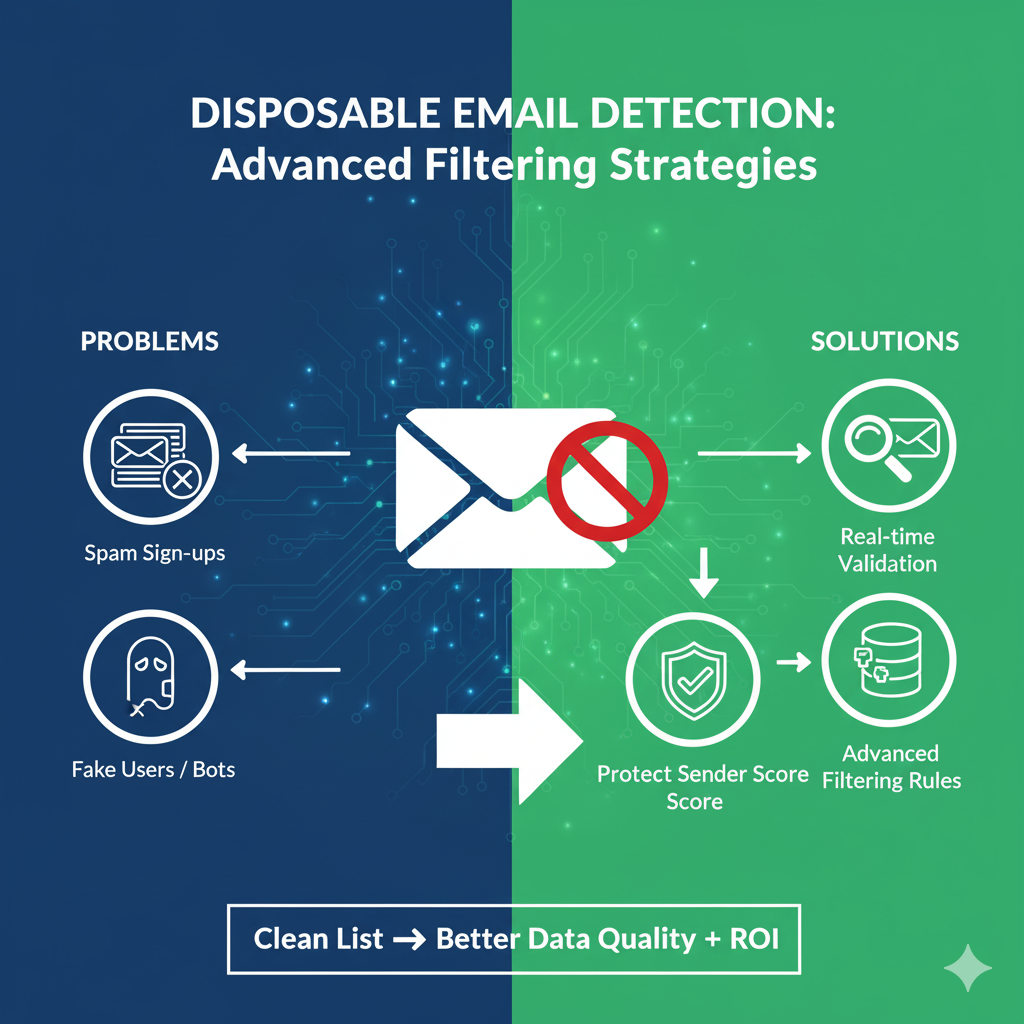
To effectively detect disposable emails, you can implement a combination of techniques like email history analysis, domain blacklisting, and real-time verification systems. Utilizing machine learning enhances filtering accuracy by identifying patterns associated with disposable addresses. Ensure you maintain a user-friendly interface and provide clear messaging to build trust. By integrating these strategies, you’ll minimize risks while improving user experience. Discover innovative approaches to boost your filtering efficiency as you explore further.
Table of Contents
Key Takeaways
- Implement email history analysis to identify patterns linked to disposable email services and prevent repeated use.
- Utilize domain blacklisting to maintain and reference an updated list of known disposable email domains during filtering.
- Integrate real-time verification systems with robust server setups to ensure quick validation of email addresses.
- Apply machine learning techniques, such as neural networks, to improve the accuracy of disposable email detection through pattern recognition.
- Focus on user experience by providing clear messaging, a simple interface, and a feedback mechanism for continuous improvement.
Understanding Disposable Email Addresses and Their Impact
Have you ever wondered why disposable email addresses are so popular? Their historical origins trace back to the need for privacy and security online. As the internet grew, so did concerns about spam and data breaches. People started seeking ways to protect their main email accounts, leading to the rise of disposable addresses. These temporary emails allow you to sign up for services without revealing your identity, offering a layer of anonymity.
The social implications of this trend are significant. While they promote privacy, they can also facilitate malicious activities, like fraud or harassment. You might find yourself navigating a complex landscape where convenience meets risk, making it crucial to understand both the benefits and pitfalls of using disposable email addresses in today’s digital world.
Key Techniques for Detecting Disposable Email Services
Detecting disposable email services requires a combination of strategies and tools that can help identify these temporary addresses. Here are four key techniques you can use:
- Email History Analysis: Check if the email has a history of being associated with disposable services. Look for patterns or repeated use.
- Syntax Checking: Validate the structure of the email address to spot common disposable domain formats.
- Domain Blacklisting: Maintain an updated list of known disposable email domains and cross-reference new registrations against it.
- Temporary Domain Detection: Identify domains that are specifically set up for temporary use by analyzing their lifespan and registration details.
Implementing Real-Time Verification Systems
Implementing real-time verification systems can significantly enhance your ability to identify disposable email addresses instantly. To get started, you need to consider your hardware requirements.
A robust server with sufficient processing power and memory will ensure quick validation of incoming email addresses.
Additionally, implementing efficient network protocols is crucial. You’ll want to use APIs that can communicate with email verification services, allowing you to verify addresses in real-time without delays.
This setup not only minimizes the risk of accepting disposable emails but also improves user experience by providing immediate feedback.
Leveraging Machine Learning for Enhanced Filtering
Machine learning offers powerful tools for enhancing the filtering of disposable email addresses.
By leveraging advanced techniques, you can significantly improve your system’s accuracy.
Here are four key strategies to consider:
- Neural Networks: Utilize deep learning models to recognize patterns in email data, identifying characteristics common to disposable addresses.
- Algorithm Optimization: Continuously refine your algorithms to adapt to new disposable email providers, ensuring your filters remain effective.
- Feature Engineering: Extract relevant features from email domains and user behavior to enhance model performance.
- Anomaly Detection: Implement models that can identify unusual patterns, flagging potential disposable accounts before they create issues.
Best Practices for Maintaining User Experience While Filtering
When filtering out disposable email addresses, it’s crucial to prioritize user experience to maintain engagement and satisfaction. You can achieve this by focusing on user privacy and thoughtful interface design. Here are some best practices to consider:
| Best Practice | Description |
| Clear Messaging | Inform users why you’re filtering emails. This builds trust. |
| Simple Interface | Keep the email input process straightforward to minimize frustration. |
| Feedback Mechanism | Allow users to report issues, enhancing their experience while ensuring continuous improvement. |
Frequently Asked Questions
How Can Disposable Emails Affect Email Marketing Campaigns?
Disposable emails can hurt your email deliverability and skew campaign analytics. They lead to inaccurate engagement metrics, wasted resources, and potentially damage your sender reputation, making it harder for your legitimate emails to reach real customers.
Are There Legal Implications for Blocking Disposable Email Addresses?
Yes, there can be legal implications for blocking disposable email addresses. You’ll need to ensure legal compliance within your jurisdiction, as different regions may have specific regulations regarding data privacy and user rights that you must consider.
Can Users Bypass Filters With VPNS or Proxies?
Yes, users can bypass filters with VPN bypass techniques or proxy evasion methods. In fact, studies show 25% of users employ these tools to access restricted services, making detection increasingly challenging for providers.
What Are Some Common Disposable Email Service Providers?
You’ll find common disposable email service providers like Temp Mail and Guerrilla Mail. They offer temporary domains and anonymous services, allowing users to create temporary addresses for quick, hassle-free email communication without revealing their identity.
How Do I Educate Users About Disposable Email Risks?
Think of disposable emails as quicksand; one wrong step, and you’re stuck! To boost user education, create engaging awareness strategies like informative workshops, eye-catching posters, and interactive quizzes that highlight the risks and consequences effectively.
Conclusion
In your quest to keep those pesky disposable emails at bay, remember that the very filters meant to protect you might just trap a few innocent users. It’s ironic, isn’t it? You’re filtering out the bad apples but might accidentally toss out the good ones, too. So, while you’re busy building your fortress of verification, don’t lose sight of the human element. After all, in a world of automation, a little empathy can go a long way.